Building compliant cloud-native banking applications with the 12 Factor methodology
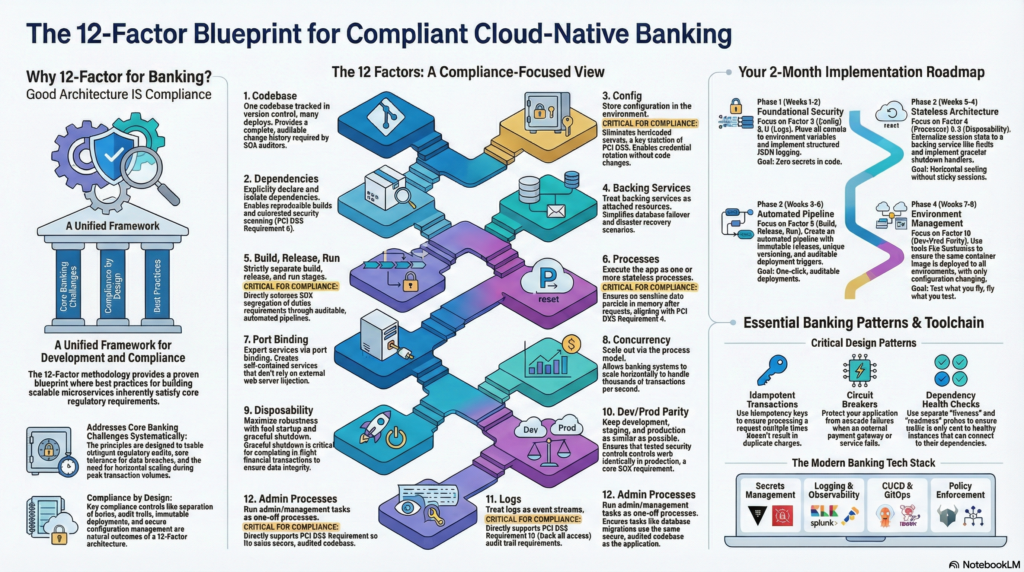
The 12 Factor App methodology remains the foundational blueprint for cloud-native development in 2025, and for junior developers entering regulated financial services, mastering these principles is non-negotiable. Originally created by Heroku co-founder Adam Wiggins in 2011, these twelve principles have evolved into the bedrock of containerized, microservices-based architectures—and they align remarkably well with banking regulatory requirements like SOX and PCI DSS. This guide provides the comprehensive technical foundation you need to build compliant, scalable banking applications on OpenShift.
Banking applications face unique challenges: stringent regulatory audits, zero tolerance for data breaches, and transaction volumes that demand horizontal scalability. The 12 Factor methodology addresses each of these concerns systematically. What makes this approach powerful is that following these principles for good software architecture simultaneously satisfies compliance requirements—separation of duties, audit trails, immutable deployments, and secure configuration management all emerge naturally from 12 Factor design.
The twelve principles that power modern banking systems
Each 12 Factor principle maps directly to OpenShift capabilities and compliance requirements. Understanding these mappings transforms abstract principles into practical implementation patterns.
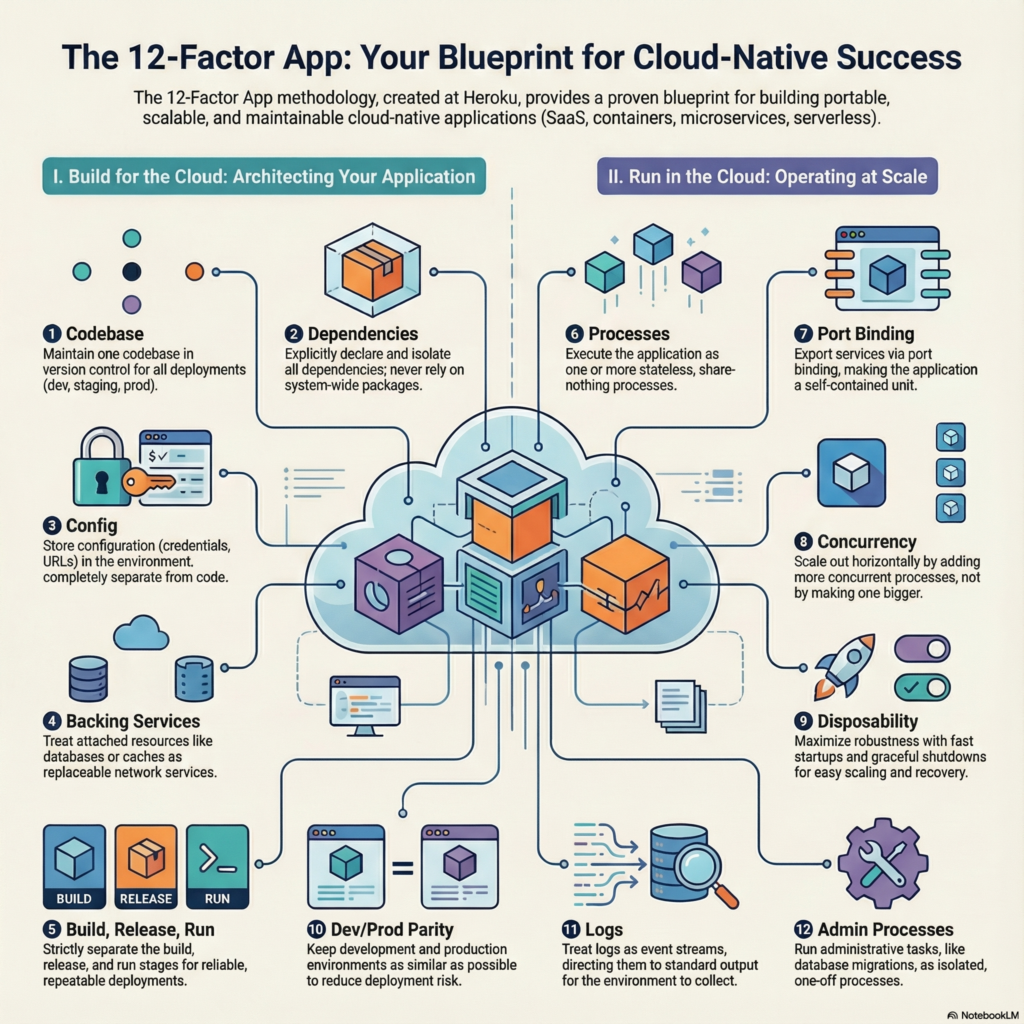
Factor 1: Codebase—one repository, many deployments
Every application maintains exactly one codebase tracked in Git, deployed to multiple environments (dev, staging, production). This principle provides the complete change history that SOX auditors require and enables GitOps workflows where every deployment is traceable to a specific commit.
OpenShift implementation: BuildConfig resources reference Git repositories directly, creating an auditable chain from source code to deployed container. Use semantic versioning (v1.2.3) and tag all production releases.
Anti-patterns to avoid: Never maintain separate “master” branches per environment, never copy code between repositories instead of creating shared libraries, and always version your Kubernetes manifests alongside application code.
Factor 2: Dependencies—explicit declaration and isolation
All dependencies must be explicitly declared in manifest files (pom.xml, package.json, requirements.txt) with pinned versions in lock files. This ensures reproducible builds critical for audit verification—you must prove that the code running in production is identical to what was tested.
Banking compliance impact: PCI DSS Requirement 6 mandates secure development practices, including vulnerability management. Explicit dependencies enable automated security scanning (SAST, SCA) in CI/CD pipelines. Generate Software Bill of Materials (SBOM) for supply chain security.
Critical rule: Never use latest tags in Dockerfiles or dependency specifications. Every production deployment must reference explicit, immutable versions.
Factor 3: Config—the linchpin of compliance
Configuration that varies between environments—database URLs, API keys, credentials—must be stored in environment variables, never in code. This single principle addresses multiple compliance requirements simultaneously.
PCI DSS alignment: Requirement 2 prohibits vendor-supplied defaults; Requirement 8 mandates unique identification and secure authentication. Externalized configuration with secrets management platforms (HashiCorp Vault, AWS Secrets Manager) satisfies both requirements while enabling credential rotation without code changes.
OpenShift implementation:
apiVersion: v1
kind: ConfigMap
metadata:
name: banking-service-config
data:
database.host: "postgresql.banking-prod.svc"
logging.level: "INFO"
api.timeout: "30000"
---
apiVersion: v1
kind: Secret
metadata:
name: banking-db-secret
type: Opaque
stringData:
username: admin
password: ${VAULT_INJECTED_PASSWORD}
Critical commands:
# Create ConfigMap from literals
oc create configmap app-config --from-literal=DATABASE_HOST=postgres://db:5432
# Create Secret from literals (will be base64 encoded automatically)
oc create secret generic db-secret \
--from-literal=username=admin \
--from-literal=password=secret123
# Link secret to service account for image pulls
oc secrets link default my-pull-secret --for=pull
Factor 4: Backing services—attached resources for banking data
Databases, message queues, caching systems, and payment gateways should be treated as attached resources accessible via URLs stored in configuration. Your application should make no distinction between a local PostgreSQL instance and an AWS RDS database—both are backing services swappable without code changes.
Banking security implications: This abstraction enables database failover without deployment changes, supports disaster recovery scenarios, and simplifies compliance with data residency requirements. Connection credentials managed externally satisfy PCI DSS Requirement 3 for data protection.
Factor 5: Build, release, run—the SOX compliance enabler
Strict separation of build, release, and run stages directly enforces SOX segregation of duties requirements. The person who writes code cannot be the same person who deploys to production—and automated pipelines make this separation auditable.
The pipeline: BuildConfig compiles code into a container image → ImageStream tags the release with a unique identifier → Deployment/DeploymentConfig executes the release in the target environment. Each stage is immutable and logged.
OpenShift BuildConfig example:
apiVersion: build.openshift.io/v1
kind: BuildConfig
metadata:
name: banking-service
spec:
source:
git:
uri: https://github.com/example/banking-service.git
ref: main
strategy:
type: Source
sourceStrategy:
from:
kind: ImageStreamTag
name: ubi8-openjdk-11:latest
namespace: openshift
env:
- name: MAVEN_ARGS
value: "-DskipTests package"
output:
to:
kind: ImageStreamTag
name: banking-service:latest
triggers:
- type: ConfigChange
- type: ImageChange
Key commands for release management:
# View rollout history (audit trail)
oc rollout history dc/banking-service
# Rollback to specific revision
oc rollout undo dc/banking-service --to-revision=2
# Start new build from source
oc start-build banking-service --follow
Factor 6: Processes—stateless design for transaction integrity
Application processes must be stateless and share-nothing. For banking applications, this means session data, authentication tokens, and transaction state must be externalized to backing services—never stored in process memory.
Why this matters for banking: Stateless processes enable horizontal scaling during peak transaction volumes, ensure no sensitive data persists in application memory after requests complete (PCI DSS Requirement 3), and allow any instance to handle any request without sticky sessions.
Session externalization to Redis:
spring:
session:
store-type: redis
redis:
namespace: banking:session
data:
redis:
host: ${REDIS_HOST:localhost}
port: ${REDIS_PORT:6379}
password: ${REDIS_PASSWORD:}
Factor 7: Port binding—self-contained services
Applications export services via port binding with embedded servers (Spring Boot’s embedded Tomcat, Express.js, Uvicorn). No external web server injection required.
OpenShift implementation: Services abstract internal port binding; Routes expose services externally with TLS termination.
apiVersion: route.openshift.io/v1
kind: Route
metadata:
name: banking-service-secure
spec:
host: banking.apps.cluster.example.com
to:
kind: Service
name: banking-service
tls:
termination: edge
insecureEdgeTerminationPolicy: Redirect
Factor 8: Concurrency—horizontal scaling for transaction volumes
Scale horizontally by adding process instances, not vertically by adding resources. Banking systems handling thousands of transactions per second require this approach—the Horizontal Pod Autoscaler (HPA) makes it automatic.
# Configure autoscaling based on CPU utilization
oc autoscale deployment/banking-service --min=3 --max=20 --cpu-percent=70
# Manual scaling for predictable peak loads
oc scale deployment/banking-service --replicas=10
Factor 9: Disposability—fast startup and graceful shutdown
Processes must start quickly (target under 30 seconds) and shut down gracefully. For banking applications, graceful shutdown means completing in-flight transactions before termination—critical for data integrity.
Spring Boot graceful shutdown configuration:
server:
shutdown: graceful
spring:
lifecycle:
timeout-per-shutdown-phase: 30s
Kubernetes probes for lifecycle management:
livenessProbe:
httpGet:
path: /actuator/health/liveness
port: 8080
initialDelaySeconds: 30
periodSeconds: 10
readinessProbe:
httpGet:
path: /actuator/health/readiness
port: 8080
initialDelaySeconds: 10
periodSeconds: 5
Factor 10: Dev/prod parity—identical environments for compliance
Minimize gaps between development and production in time, personnel, and tools. Use identical container images across all environments—only configuration changes. This ensures tested controls work identically in production, a core SOX requirement.
OpenShift environment management with Kustomize:
├── base/
│ ├── kustomization.yaml
│ ├── deployment.yaml
│ └── service.yaml
├── overlays/
│ ├── dev/
│ │ └── kustomization.yaml
│ ├── test/
│ │ └── kustomization.yaml
│ └── prod/
│ ├── kustomization.yaml
│ └── replica-patch.yaml
Production overlay (overlays/prod/kustomization.yaml):
apiVersion: kustomize.config.k8s.io/v1beta1
kind: Kustomization
resources:
- ../../base
namespace: banking-prod
commonLabels:
environment: production
patches:
- path: replica-patch.yaml
Apply with: oc apply -k overlays/prod
Factor 11: Logs—the regulatory mandate
Applications must write all logs to stdout/stderr as unbuffered event streams. The execution environment handles aggregation, routing, and retention. This principle directly supports PCI DSS Requirement 10 (track and monitor all access) and SOX audit trail requirements.
Regulatory retention requirements:
- PCI DSS: Minimum 1 year retention, 3 months immediately available
- SOX: 7 years retention for financial transactions and system changes
What must be logged for compliance:
- All authentication attempts (success and failure)
- Access to cardholder data and financial records
- Administrative actions and privilege escalation
- System component changes
- Security events and alerts
Spring Boot structured JSON logging:
# Spring Boot 3.4+ native structured logging
logging.structured.format.console=ecs
logging.structured.ecs.service.name=banking-service
logging.structured.ecs.service.environment=${ENVIRONMENT:development}
Correlation ID implementation for distributed tracing:
@Component
@Order(Ordered.HIGHEST_PRECEDENCE)
public class CorrelationIdFilter extends OncePerRequestFilter {
@Override
protected void doFilterInternal(HttpServletRequest request,
HttpServletResponse response,
FilterChain chain) throws ServletException, IOException {
String correlationId = request.getHeader("X-Correlation-Id");
if (correlationId == null) {
correlationId = UUID.randomUUID().toString();
}
MDC.put("correlationId", correlationId);
response.setHeader("X-Correlation-Id", correlationId);
try {
chain.doFilter(request, response);
} finally {
MDC.remove("correlationId");
}
}
}
Factor 12: Admin processes—secure one-off tasks
Administrative tasks (database migrations, console sessions, data corrections) run as one-off processes using the same codebase and configuration as the application. Kubernetes Jobs and CronJobs implement this pattern.
Database migration Job:
apiVersion: batch/v1
kind: Job
metadata:
name: banking-db-migration
spec:
template:
spec:
containers:
- name: migration
image: banking-service:1.2.3
command: ["./run-migrations.sh"]
envFrom:
- secretRef:
name: banking-db-secret
restartPolicy: OnFailure
backoffLimit: 3
Critical rule: Never run migrations during application startup. Execute them as separate Jobs before deployment to maintain clean separation and enable rollback.
OpenShift security features for banking compliance
OpenShift provides enterprise security features beyond standard Kubernetes that directly support banking compliance requirements.
Security Context Constraints control pod permissions
SCCs are OpenShift’s mechanism for controlling what actions pods can perform. Banking applications should use the most restrictive SCC possible.
# List available SCCs (from most to least restrictive)
oc get scc
# Common SCCs:
# restricted-v2 - Default, most restrictive
# nonroot-v2 - Requires non-root user
# anyuid - Allows running as any user
# privileged - Full access (avoid in banking)
# Add SCC to service account (only when necessary)
oc adm policy add-scc-to-user nonroot -z banking-service-sa -n banking-prod
Network policies implement PCI DSS segmentation
Network policies enforce PCI DSS network segmentation requirements at the Kubernetes level:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: banking-service-policy
namespace: banking-prod
spec:
podSelector:
matchLabels:
app: banking-service
policyTypes:
- Ingress
- Egress
ingress:
- from:
- namespaceSelector:
matchLabels:
network.openshift.io/policy-group: ingress
ports:
- port: 8080
egress:
- to:
- podSelector:
matchLabels:
app: postgresql
ports:
- port: 5432
RBAC enforces least privilege access
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: banking-deployer
namespace: banking-prod
rules:
- apiGroups: ["apps"]
resources: ["deployments"]
verbs: ["get", "list", "watch", "update", "patch"]
- apiGroups: [""]
resources: ["configmaps", "secrets"]
verbs: ["get", "list", "watch"]
# Note: No create/delete for secrets in production
Practical patterns for banking microservices
Idempotent transaction processing
Financial transactions must be idempotent—processing the same request twice must not result in duplicate charges. Implement using idempotency keys:
@Service
public class TransactionService {
private final TransactionRepository repository;
private final RedisTemplate<String, String> redisTemplate;
private static final Duration IDEMPOTENCY_TTL = Duration.ofHours(24);
@Transactional
public TransactionResult processPayment(String idempotencyKey, PaymentRequest request) {
String cacheKey = "idempotency:" + idempotencyKey;
String existingResult = redisTemplate.opsForValue().get(cacheKey);
if (existingResult != null) {
log.info("Returning cached result for idempotency key: {}", idempotencyKey);
return objectMapper.readValue(existingResult, TransactionResult.class);
}
// Process new transaction
Transaction transaction = Transaction.builder()
.idempotencyKey(idempotencyKey)
.amount(request.getAmount())
.status(TransactionStatus.PENDING)
.build();
Transaction saved = repository.save(transaction);
TransactionResult result = executePayment(saved);
// Cache result for idempotency
redisTemplate.opsForValue().set(cacheKey,
objectMapper.writeValueAsString(result), IDEMPOTENCY_TTL);
return result;
}
}
Circuit breaker for payment gateway resilience
External payment gateways fail. Circuit breakers prevent cascade failures:
resilience4j:
circuitbreaker:
instances:
paymentGateway:
slidingWindowSize: 20
failureRateThreshold: 50
waitDurationInOpenState: 30s
permittedNumberOfCallsInHalfOpenState: 5
retry:
instances:
paymentGateway:
maxAttempts: 3
waitDuration: 1s
enableExponentialBackoff: true
exponentialBackoffMultiplier: 2
@CircuitBreaker(name = "paymentGateway", fallbackMethod = "paymentFallback")
@Retry(name = "paymentGateway")
public PaymentResult processPayment(PaymentRequest request) {
return paymentGatewayClient.process(request);
}
private PaymentResult paymentFallback(PaymentRequest request, Exception ex) {
log.error("Payment gateway unavailable, queuing for retry", ex);
return PaymentResult.pendingRetry(request.getTransactionId());
}
Health checks with dependency verification
Separate liveness (is the process alive?) from readiness (can we serve traffic?):
@Component
public class PaymentGatewayHealthIndicator implements HealthIndicator {
@Override
public Health health() {
try {
boolean reachable = paymentGatewayClient.healthCheck()
.timeout(Duration.ofSeconds(5))
.block();
return reachable
? Health.up().withDetail("gateway", "reachable").build()
: Health.down().withDetail("gateway", "unreachable").build();
} catch (Exception e) {
return Health.down().withException(e).build();
}
}
}
Configure probes to use appropriate endpoints:
management:
endpoint:
health:
probes:
enabled: true
group:
liveness:
include: livenessState
readiness:
include: readinessState,db,redis,paymentGateway
Database connection pooling for high-throughput transactions
spring:
datasource:
url: ${DATABASE_URL}
hikari:
maximum-pool-size: ${DB_POOL_SIZE:20}
minimum-idle: ${DB_POOL_SIZE:20}
connection-timeout: 30000
idle-timeout: 600000
max-lifetime: 1800000
pool-name: BankingHikariPool
register-mbeans: true
Implementation roadmap for junior developers
Phase 1: Foundation (weeks 1-2)
Start with Factor 3 (Config) and Factor 11 (Logs)—these have immediate compliance impact and are straightforward to implement.
- Action items: Audit your codebase for hardcoded credentials and move them to environment variables. Implement structured JSON logging with correlation IDs.
- Success metric: Zero secrets in source code; all logs in JSON format to stdout.
Phase 2: Stateless architecture (weeks 3-4)
Implement Factor 6 (Processes) and Factor 9 (Disposability).
- Action items: Externalize session storage to Redis. Implement graceful shutdown handlers. Configure Kubernetes liveness and readiness probes.
- Success metric: Application can scale to multiple replicas without sticky sessions; shutdown completes in-flight requests.
Phase 3: Build pipeline (weeks 5-6)
Implement Factor 5 (Build, Release, Run) with proper separation.
- Action items: Create BuildConfig for automated builds. Implement ImageStream tagging strategy. Configure deployment triggers.
- Success metric: Immutable releases with unique identifiers; automated rollback capability.
Phase 4: Environment management (weeks 7-8)
Implement Factor 10 (Dev/Prod Parity) with Kustomize or Helm.
- Action items: Create base manifests and environment overlays. Standardize backing services across environments. Implement namespace strategy.
- Success metric: Same container image deploys to all environments; configuration-only differences between environments.
Common challenges in banking environments
Challenge 1: Legacy system integration. Many banking systems integrate with mainframes or legacy databases. Treat these as backing services (Factor 4) with clean abstraction layers and circuit breakers.
Challenge 2: Change Advisory Board (CAB) processes. Traditional weekly CAB meetings conflict with continuous deployment. Work with compliance teams to implement automated policy gates that satisfy CAB requirements—tools like Open Policy Agent can enforce governance rules in pipelines.
Challenge 3: Audit evidence collection. Automate audit trail generation. Every deployment should automatically generate evidence: Git commit SHA, build logs, test results, approval records, deployment timestamps.
Essential tools for cloud-native banking development
- Secrets management: HashiCorp Vault, AWS Secrets Manager (both PCI DSS Level 1 certified)
- Logging: ELK Stack, Splunk, Datadog (with tamper-proof storage for compliance)
- Observability: OpenTelemetry, Prometheus/Grafana
- Policy enforcement: Open Policy Agent, Kyverno
- CI/CD: ArgoCD (GitOps), Tekton (cloud-native pipelines)
Conclusion
The 12 Factor App methodology provides junior developers with a proven framework for building banking applications that are simultaneously cloud-native and compliant. The key insight is that good architecture and regulatory compliance are not opposing forces—they reinforce each other.
Factor 3 (Config) eliminates hardcoded credentials that violate PCI DSS. Factor 5 (Build, Release, Run) enforces the segregation of duties that SOX requires. Factor 11 (Logs) creates the audit trails that regulators demand. By following these principles, you build applications that scale horizontally during peak transaction volumes, recover gracefully from failures, and pass compliance audits with documented evidence.
OpenShift’s native support for ConfigMaps, Secrets, BuildConfigs, ImageStreams, and Security Context Constraints means you’re not fighting the platform—you’re leveraging it. Start with configuration externalization and structured logging in your first sprint. Add stateless session management and proper health checks next. Build out your CI/CD pipeline with immutable releases. Within two months, you’ll have a 12 Factor-compliant banking application that satisfies SOX and PCI DSS requirements by design.
The transition from legacy monoliths to cloud-native microservices is challenging, but the 12 Factor methodology provides a clear path. Each principle you implement reduces operational risk, improves scalability, and strengthens your compliance posture. For junior developers in financial services, mastering these twelve principles is the foundation of a successful cloud-native career.